
 |

|
| ActiveWin: Reviews | Active Network | New Reviews | Old Reviews | Interviews |Mailing List | Forums |
|
|
|
|
|
DirectX |
|
ActiveMac |
|
Downloads |
|
Forums |
|
Interviews |
|
News |
|
MS Games & Hardware |
|
Reviews |
|
Support Center |
|
Windows 2000 |
|
Windows Me |
|
Windows Server 2003 |
|
Windows Vista |
|
Windows XP |
|
|
|
|
|
|
|
News Centers |
|
Windows/Microsoft |
|
DVD |
|
Apple/Mac |
|
Xbox |
|
News Search |
|
|
|
|
|
|
|
ActiveXBox |
|
Xbox News |
|
Box Shots |
|
Inside The Xbox |
|
Released Titles |
|
Announced Titles |
|
Screenshots/Videos |
|
History Of The Xbox |
|
Links |
|
Forum |
|
FAQ |
|
|
|
|
|
|
|
Windows XP |
|
Introduction |
|
System Requirements |
|
Home Features |
|
Pro Features |
|
Upgrade Checklists |
|
History |
|
FAQ |
|
Links |
|
TopTechTips |
|
|
|
|
|
|
|
FAQ's |
|
Windows Vista |
|
Windows 98/98 SE |
|
Windows 2000 |
|
Windows Me |
|
Windows Server 2002 |
|
Windows "Whistler" XP |
|
Windows CE |
|
Internet Explorer 6 |
|
Internet Explorer 5 |
|
Xbox |
|
Xbox 360 |
|
DirectX |
|
DVD's |
|
|
|
|
|
|
|
TopTechTips |
|
Registry Tips |
|
Windows 95/98 |
|
Windows 2000 |
|
Internet Explorer 5 |
|
Program Tips |
|
Easter Eggs |
|
Hardware |
|
DVD |
|
|
|
|
|
|
|
ActiveDVD |
|
DVD News |
|
DVD Forum |
|
Glossary |
|
Tips |
|
Articles |
|
Reviews |
|
News Archive |
|
Links |
|
Drivers |
|
|
|
|
|
|
|
Latest Reviews |
|
Xbox/Games |
|
Fallout 3 |
|
|
|
Applications |
|
Windows Server 2008 R2 |
|
Windows 7 |
|
|
|
Hardware |
|
iPod Touch 32GB |
|
|
|
|
|
|
|
Latest Interviews |
|
Steve Ballmer |
|
Jim Allchin |
|
|
|
|
|
|
|
Site News/Info |
|
About This Site |
|
Affiliates |
|
Contact Us |
|
Default Home Page |
|
Link To Us |
|
Links |
|
News Archive |
|
Site Search |
|
Awards |
|
|
|
|
|
|
|
Credits |


|
Product: Norton Internet Security 2002 Company: Symantec Website: http://www.symantec.com Estimated Street Price: $69.95 Review By: Julien Jay |
Advanced Features
|
Table Of Contents |
Norton Internet Security 2002 allows advanced and expert users to define advanced options such as authorized HTTP ports, firewall rules and much more. Users are guided step-by-step to create new rules and when a rule alert appears, for example if you try for the first time to update your Microsoft Money online financial data, users are prompted to create a new rule for this event (if they haven’t done it before) in order to prevent the alert to be redisplayed each time they use Money. Plus this configuration warning lets you specify if this program should be authorized to access the Internet while being used by other members of the family. The AutoBlock feature of Norton Internet Security 2002 will automatically shut off communication from every hacker that might intrude into your PC. But you can also choose to always block (or for a defined length) a specific IP address to prevent the remote user to access your computer. Even if you may want to block hackers from accessing your computer you don’t obviously wish to block everyone especially if you have a FTP server running on your machine. Thankfully, the flexibility of Norton Internet Security 2002 will let you authorize inbound connections from authenticated and trusted sources while blocking hackers.
Norton Internet Security 2002 should be updated on a regular basis in order to make sure you’ve got the latest protection rules, minor patches, etc. It comes with a one year free update subscription which you can retrieve using the brand new version 1.62 of LiveUpdate. After that you’ll have to pay the sum of $6.95 to renewal your subscription which is ridiculous since at the time your subscription will expire (if ever it expires) a new version of Norton Internet Security will be out. By blocking and monitoring all the outbound/inbound Internet ports Norton Internet Security 2002 is your PC’s bodyguard that will protect it from hackers’ attacks. It’s clear that the FireWall included in Microsoft Windows XP can’t compete with Symantec Norton Internet Security 2002.
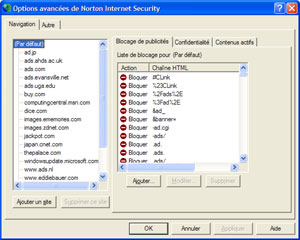
Norton Internet Security 2002 Advanced Settings (click to
enlarge)
Reports
NIS will report in a very accurate and complete window all your Internet security statistics (blocked websites, blocked pictures…) as shown below (you’ll be able to print them).
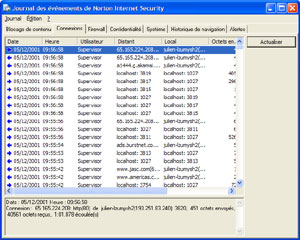
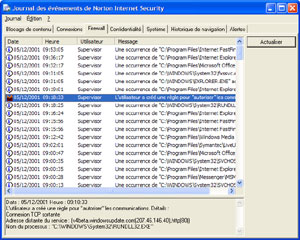
Norton
Internet Security 2002 Log (click to enlarge)
It tracks every Internet connection, every visited website, every program that uses Internet; such as Microsoft Outlook, Microsoft Money and much more. Every attack attempt is saved along with the IP address of the hacker. However, Norton Internet Security 2002 can’t trace the IP address itself so you’ll have to trace it using third party program.
Is It Useful?
Norton Internet Security 2002 really works and protects you, your children and your family from all Internet threats. Norton Internet Security 2002 definitely stays the best firewall and is much better than CyberPatrol for filtering web sites. More, it really protects your privacy and once again this works! If you try to send private information that you have defined NIS will block them until you agree to send them (and have the adequate privileges to do so). All Internet users, from the cool surfer to the passionate one should use it and particularly those with cable or ADSL connections. You can try it for free by downloading a preview Trial version at http://www.symantec.com/trial
Real Tests
To ensure that Norton Internet Security 2002 is a high-quality product we tested it by connecting a machine to the ‘Net and trying to hack it using various methods through another machine. The first thing we noticed is that Norton Internet Security 2002 really monitors every one of your currently running software programs that may access the Internet connection without your knowledge and alerts you. Indeed we've seen that Microsoft Windows Media Player 7.1/8.0 may try to connect to the ‘Net to check for updates without you even asking it to do so: in that case Norton asks you what to do and if it should permit or not this network communication. We repeated the test with Napster (here if someone is trying to pickup a MP3 file on your computer Norton Internet Security gives you an alert asking what to do), PC-Cillin (viruses updates), Copernic 2001 Pro, CuteFTP Pro, FrontPage 2002, and many other software like the MSN Zone games (chess, checkers, etc.) and Norton Internet Security 2002 each time warned us about the fact that a software was trying to use our connection. Sure you can create rules that will always authorize these network communications in order to avoid multiple alerts.
Since version 2.5 each time a program attempts to access the ‘Net you’re prompted to create a rule for this program in order to let it access the ‘Net or not. The benefit is that you can be sure no Trojan horses mask themselves as one of those applications so they can’t pass through your defense. Now you can even catalog rules by software categories for a much more accurate management. Concerning the hack problem the first thing we have tested is a basic threat: we enabled the Windows Folders sharing feature and we attempted to connect to the machine using its IP address and the name of the shared folder: when we tried to pick up a file or to remove one on the Norton protected PC we were instantly alerted about the fact that someone was trying to access the computer (sure you can decide to authorize or not this communication). Then we tested Norton Internet Security 2002 with serious tools that serious hackers used to pirate a computer.
We first ping our Norton Protected PC using BO2k (BackOrifice: a program that uses a hoax to enter a computer by an opened port) and the software displays a security alert (same thing when you try to perform a ping through the native Windows 2000/XP command) on the remote PC that prevents us from reaching it. Every security alert event is logged with the IP address of the machine that tried to ping you in a text file you can later browse. Using Trojan horses programs like SubSeven and Backdoor we were unable to access the Norton protected PC as Norton Internet Security 2002 always detect our numerous attempts to hack it. Last thing we did is to test the firewall with some programs that aren't malicious ones but that require an Internet connection to display advertisement banner: for PKZip we were instantly alerted as well as for DAP (Download Accelerator Plus).
However this wasn't the case for FileFerret a freeware that displays ads: however the treat isn't harmful so we don't blame Norton Internet Security for not alerting users for this outbound. Finally at the privacy level we were impressed by the Norton Internet Security 2002 ability to really protect our privacy by blocking some cookies, hiding email address, etc. Using these features and by completing the data to protect form we were able to access almost all our usual websites we like except one. If you asked Norton Internet Security to protect your phone number and if you type it in a web form to send it over the ‘Net you'll receive an alert asking what to do. In conclusion our test results are more than good and show that Norton Internet Security 2002 has a very good engine and that its sensitivity isn't too great in order to avoid annoying user by detecting false threats.
Compatibility
Even if Norton Internet Security 2002 is great software it actually features
some nasty bugs. For example, NIS 2002 blocks without warning (and it
doesn’t demand the user what to do) some applications that might access the
internet like the MusicMatch JukeBox 6.1/7 updater, Windows Media Player 8
Speaker Enhancement Updater, etc. If this new version solves the
compatibility issue with the Alcatel SpeedTouch USB ADSL modem it adds
numerous issues with websites that strangely can’t process the information
you enter because NIS 2002 is active.
Another drawback is that
NIS 2002 doesn't automatically disable the native Windows XP firewall: so if
you don't manually do so, both firewall may enter in conflict.



