|

|
| ActiveWin: Reviews | Active Network | New Reviews | Old Reviews | Interviews |Mailing List | Forums |
|
|
|
|
|
DirectX |
|
ActiveMac |
|
Downloads |
|
Forums |
|
Interviews |
|
News |
|
MS Games & Hardware |
|
Reviews |
|
Support Center |
|
Windows 2000 |
|
Windows Me |
|
Windows Server 2003 |
|
Windows Vista |
|
Windows XP |
|
|
|
|
|
|
|
News Centers |
|
Windows/Microsoft |
|
DVD |
|
Apple/Mac |
|
Xbox |
|
News Search |
|
|
|
|
|
|
|
ActiveXBox |
|
Xbox News |
|
Box Shots |
|
Inside The Xbox |
|
Released Titles |
|
Announced Titles |
|
Screenshots/Videos |
|
History Of The Xbox |
|
Links |
|
Forum |
|
FAQ |
|
|
|
|
|
|
|
Windows XP |
|
Introduction |
|
System Requirements |
|
Home Features |
|
Pro Features |
|
Upgrade Checklists |
|
History |
|
FAQ |
|
Links |
|
TopTechTips |
|
|
|
|
|
|
|
FAQ's |
|
Windows Vista |
|
Windows 98/98 SE |
|
Windows 2000 |
|
Windows Me |
|
Windows Server 2002 |
|
Windows "Whistler" XP |
|
Windows CE |
|
Internet Explorer 6 |
|
Internet Explorer 5 |
|
Xbox |
|
Xbox 360 |
|
DirectX |
|
DVD's |
|
|
|
|
|
|
|
TopTechTips |
|
Registry Tips |
|
Windows 95/98 |
|
Windows 2000 |
|
Internet Explorer 5 |
|
Program Tips |
|
Easter Eggs |
|
Hardware |
|
DVD |
|
|
|
|
|
|
|
ActiveDVD |
|
DVD News |
|
DVD Forum |
|
Glossary |
|
Tips |
|
Articles |
|
Reviews |
|
News Archive |
|
Links |
|
Drivers |
|
|
|
|
|
|
|
Latest Reviews |
|
Xbox/Games |
|
Fallout 3 |
|
|
|
Applications |
|
Windows Server 2008 R2 |
|
Windows 7 |
|
|
|
Hardware |
|
iPod Touch 32GB |
|
|
|
|
|
|
|
Latest Interviews |
|
Steve Ballmer |
|
Jim Allchin |
|
|
|
|
|
|
|
Site News/Info |
|
About This Site |
|
Affiliates |
|
Contact Us |
|
Default Home Page |
|
Link To Us |
|
Links |
|
News Archive |
|
Site Search |
|
Awards |
|
|
|
|
|
|
|
Credits |

|
Product: Windows Server 2003 |
|
Active Directory
| Table Of Contents |
| 1:
Introduction 2: Pricing & System Requirements 3: New Features 4: Creation of ADAM 5: Active Directory 6: Security 7: IIS 6 8: Terminal Services 9: Conclusion |
Active Directory is the Directory Service for Microsoft Networks. There have a few changes to AD that you should be aware of.
The first that I will mention has to do with clients. For those of you still holding on to that 8-year old Windows 95, it’s time to say goodbye. Windows 2003’s implementation of AD will not support it; the proof is given to you when you run DCPromo.
The AD Database in Windows 2000 is split into three distinct partitions: Domain, Configuration and Schema.
1. The Domain Partition holds all objects that have been created within AD (Users, Computers, Groups, Organizational Units, etc…) and the attributes associated with each object. (A User may have a password or Last Name attribute associated with it, but an Organizational Unit or Computer would not.)
2. The Configuration Partition holds all settings for the forest relating to Site Configuration or other applications that you may have on the network, like Exchange Server.
3. The Schema Partition contains the Classes for the Active Directory of the specific network that you are on. (Login scripts and Group Policies are not part of the directory, but are replicated within the file system.) If you don’t understand what a class is, then allow me to elaborate.
Think of a Contact in Microsoft Outlook. (A Contact is a Form, not a class, but you should get my point.) If you have ever used Outlook 2000 and saw all of the fields that are available to you when you created a new contact, then try to imagine a new Contact as the Class and the Fields available to you as the Attributes. When you upgraded to Outlook 2003, you would see at least one new field, the Picture Field, which you can use to bind an image to a Contact. Think of that as an additional attribute for the Contact Class. When that attribute is added to Outlook as the upgrade takes place, then not only do the new Contacts have that field exposed to them, but the old ones do as well.
Active Directory for Windows 2003 is divided into Four Partitions now. Here is a breakdown of the four partitions:
1. Domain – This partition hold objects that are specific to the domain that they were created in. Information created in this domain is only replicated to other Domain Controllers within the domain.
2. Configuration – This partition contains information about the configuration of your forest. This partition is replicated to all Domain Controllers in the forest.
3. Schema – Here you will find the classes for all potential objects in the forest. The contents of this partition are also replicated to every Domain Controller in the Forest.
4. Application – This partition is new to Windows 2003 Server. The information stored in this partition is replicated to all other Domain Controllers within its domain, and to selective Domain Controllers within the forest.
There are also numerous enhancements. For example, you can now select multiple user objects and modify their attributes simultaneously. You can save Active Directory Queries as XML Files. AD has added attributes that allow provide you with the ability to map an AD User Object to a Passport Account, if they have one. This is similar to the method that Windows XP uses to bind your passport to your XP Account. The only catch is that IIS 6.0 needs to be installed for the HTTP request. Whether IIS needs to be on all DC’s for the Authentication Process to occur throughout the forest seems likely, but I am not certain so you may want to ask a Microsoft Rep at one of the release events. (I read this in a Windows 2003 Server technical whitepaper on AD in 2003. I haven’t seen how to do this….yet.)
There is no longer a need to have a Global Catalog Server at each branch office. A DC in a remote office has the ability to now cache Universal Group Membership for users at that location so that they don’t need to access a GC if the connection to the main office is unreliable.
Windows 2003 Server Forest Native Mode is another new option for 2003 that will change the way that group membership works within a forest. Membership of groups is moved to the member level rather than a collection of users to a single unit as Microsoft puts it. 2003 Server Forest Native Mode also enhances the replication capabilities by using an improved algorithm that is present on 2003 Servers, but not activated until promotion of the directory occurs. As in Windows 2000, once you promote the Functionality level, no Pre-Windows 2003 Server can be a DC…
Deploying Windows 2003 Servers are much easier with enhancements like the ability to install a Replica from Media. What this means is that you may create a copy of the Windows 2003 Active Directory and ship that CD to a branch office.
If the Directory is large, you may be able to save several MB’s over your network connections and also several man hours spent waiting for the Directory to replicate.
NOTE: If you wish to accomplish this, you need to run the /adv switch while executing dcpromo on the 2003 Server. Ex: dcpromo /adv
DNS Zones have been moved to the Application Partition of Active Directory, which alleviates the load on Global Catalog Servers. Previously GC’s would hold a subset of information for the entire forest, including DNS Records if the zones were AD-integrated. Now, since the DNS zones are stored in the Application Partition, the records are sent to all DC’s in the domain, and selective DC’s in the forest that are external to the source domain.
DOMAIN RENAMING – Now I know that some of you have been waiting for this! Windows 2003 gives you the ability to rename a domain. That is right; you can change the DNS or NetBIOS names of your domain! It’s not a nice or convenient process however. Once you change the name of your domain, you must reboot every server in the domain, you must also reboot all members of the domain twice. Microsoft says that you shouldn’t do this on a routine basis… Also, you still can not change which domain is the Forest Root Domain. (This would be the one containing those nice Enterprise Admins and Schema Admins security groups.) You are able to create Forest Trusts however, which creates two-way transitive trusts between all domains in two forests. ADMT has been improved to help ease the process of moving user accounts between domains.
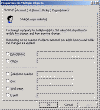
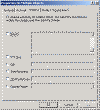
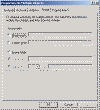
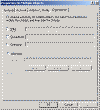
Speaking of User Accounts, there are two enhancements to User Account Management. The first is the ability to Drag and Drop User Accounts between Containers in AD. The other is the ability to select multiple users and make modifications to their account simultaneously. This is convenient for ASP’s or even Admins when a department may move locations and you need to update account address information. There is only one thing that I wish they would have done: Given us the ability to reset passwords on multiple accounts to the same thing… Here are some screens:
If you are planning on upgrading from a 2000 Directory Service to a 2003 Directory Service, you must first run a utility called adprep.exe. The Adrep utility must be run on an existing Windows 2000 Domain and the user has to be logged on as an Enterprise Administrator and must also be able to modify the schema of Active Directory. AdPrep prepares a Windows 2000 Active Directory for the migration. If you are upgrading from NT 4 to 2003, there is no need to use AdPrep as no Directory exists in NT 4. This utility extends the schema for 2003. ADPrep can be found on the Windows 2003 Server CD and must be run in two phases on a 2000 Domain Controller before a 2003 Server can be made a domain controller. Phase one is with the /ForestPrep switch and you guessed it, it prepares the schema of the forest. Stage two of the utility is with the /DomainPrep switch and runs a lot faster.
There is also a new Replication Trust Monitoring utility that lets you monitor the status of replication between DC’s in your Network.
THE GROUP POLICY MANAGEMENT CONSOLE
The GPMC provides a more precise amount of control to administrators when it comes to managing Group Policies. From this one interface, an administrator can manage the GPO’s for an organization, print out HTML reports that detail settings, results and modeling data. This tool is not available with Windows 2003 Server, but will be available shortly after commercial release as a download. At the time of this writing, I had just received my copy from my MSDN monthly shipment. The GPMC can be run off of a Windows 2003 Server or a Windows XP client with SP1, an additional hotfix and the .Net framework installed.
Microsoft states that there are over 150 new policy settings included with
Windows 2003 Server’s version of Active Directory. To assist with all of
the modifications, Microsoft has provided a revised MMC for GPO’s that
displays the description of any settings in a GPO. There are two new
utilities that Microsoft provides that will give an administrator the
ability to see the affects of a specific Group Policy. One such utility is
Group Policy Results and the other is Group Policy Modeling. They
essentially do the same things; the difference is when the report is given.
With Group Policy Results, you can see what settings a specific user will
receive when they log into the network. Group Policy results will display
the current settings based on the current GPO’s that the user is affected
by. Group Policy Modeling is the second new utility that can help with
Group Policy Objects. Group Policy Modeling shows an administrator what
effects a specific GPO will have on specified users.